Hello!
In this project, I used tools such as tcpdump and Wireshark to capture and analyze packets for a cleartext password using a purposeful unencrypted site. Obviously, almost all data is encrypted and uses some form of additional security but for purposes of this project, I am not using it. This project also let me get my hands wet with the Wireshark application and really understand more concepts from my Network+ certification.
The first thing I did was fire up my Kali VM box and open up a terminal where tcpdump is already installed. Next, I ran the ifconfig command to find the names of interfaces and other configurations for my Kali box. The first interface, eth0, is mine, and the second, lo, is the loopback address. This will be useful later in the project to understand communication between host and destination traffic.
To capture packets I ran the following command: $ sudo tcpdump – eth0 -w ClearTraffic.txt
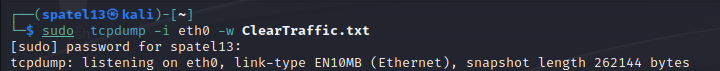
What this is doing is having all traffic captured from the interface eth0 which is mine as discussed earlier, and writing it out in a file called “ClearTraffic.txt”.
As traffic is in the process of being captured, I visited an unencrypted login site that was set up for this purpose. Since it’s unencrypted, I’m able to capture and read everything in clear text. Since this site is used for project purposes, I entered a fake username and password that would get denied but still get captured for analysis. I used the password “IEat”.
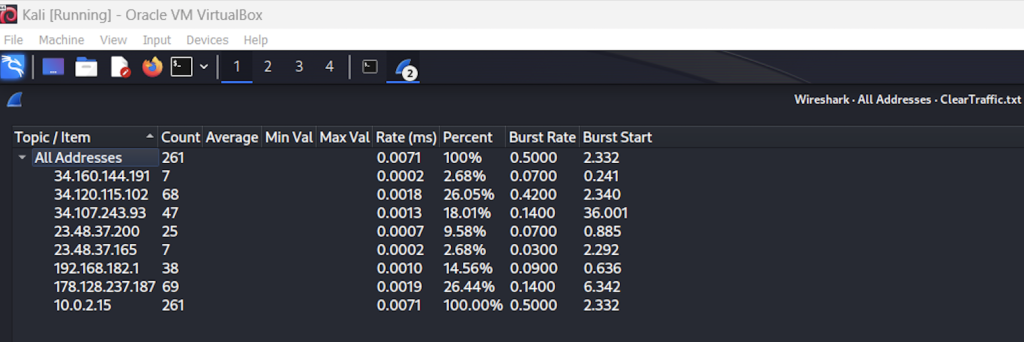
Next, I stopped the capture in the Kali terminal and opened up the Wireshark application. I loaded up my ClearTraffic.txt file for the traffic I captured via tcpdump. Before looking into the text, I wanted to understand some statistics and move around the application more. I first went to IPv4 statistics and saw all IP addresses and the number of packets received with each IP. I am focusing on two which are 10.0.2.15 (Kali IP) and 178.128.237.187 (bowtiedcyber.xyz).
Next, I went into the conversation statistics and glanced over all the tabs but finished with the TCP conversations. Here I can see almost all TCP communications between 10.0.2.15 and 178.128.237.187. The first thing I noticed was the port for the destination being 80 which is HTTP for cleartext web traffic.
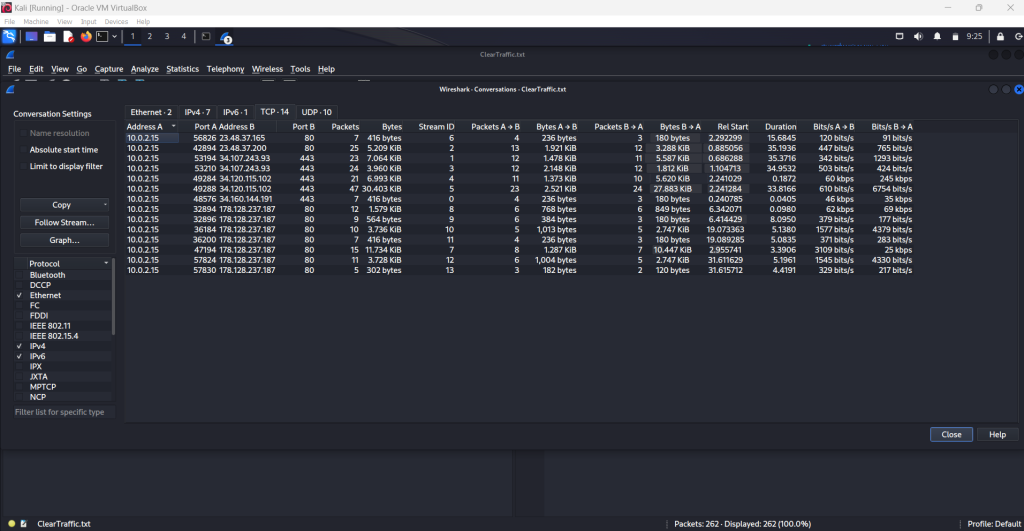
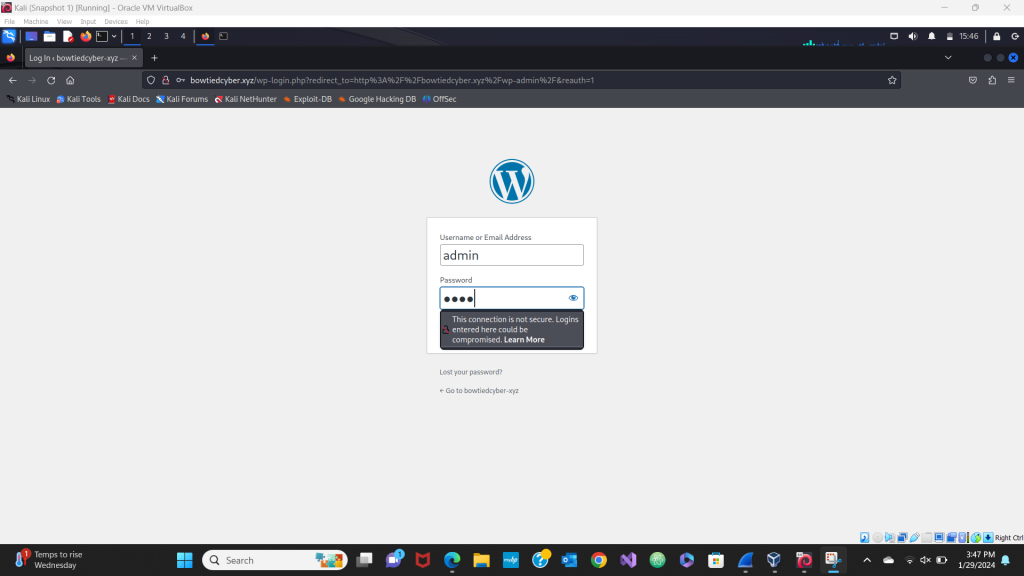
I applied a filter to follow the TCP stream and saw all the traffic labeled in yellow. Another filter I used for the purpose of this project was “tcp contains ‘login'”. This returned all packets with that keyword inside them so I could see my login attempt and failure in cleartext. As you can see on the last line in red, the login I used was “admin” and the password I used was “IEat”.
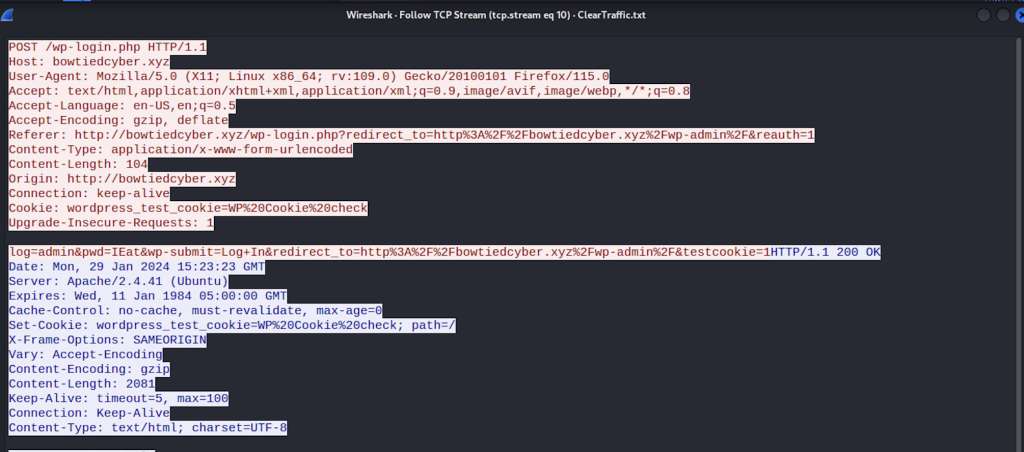
This was a very successful project with lots of road bumps but that’s where the learning really happens. It was good to utilize tcpdump and get into Wireshark itself. I’m excited to dive into the application even more for future learning.
Thanks for reading along!