In this Home-Lab setup, I go through the tasks to set up a Wazuh platform, onboard the Windows agent, and implement a File Integrity monitoring use case. My goal was to replicate a scenario that would be seen by a SOC or Security Analyst.
This was my first time getting hands-on with Wazuh’s security platform which has helped many organizations with log data analysis, endpoint detection and response, file integrity monitoring, compliance monitoring, and much more.
In this lab, I set up File Integrity monitoring use case as it’s essential for securing a system. Some important factors are:
- Unauthorized Changes Detection
- Compliance Requirements
- Insider Threat Mitigation
After downloading the Wazuh OVA file into the VM, the most important task in the configuration was changing the network settings to Bridge mode so my host device could access it directly.
Following the login process, I ran ifconfig the get the IP address for the server which I then entered into the browser.
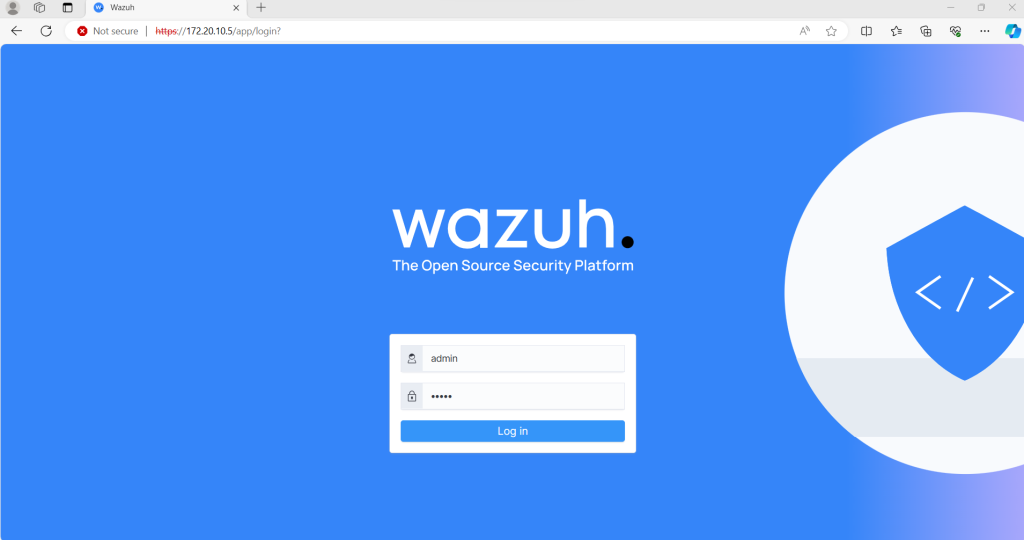
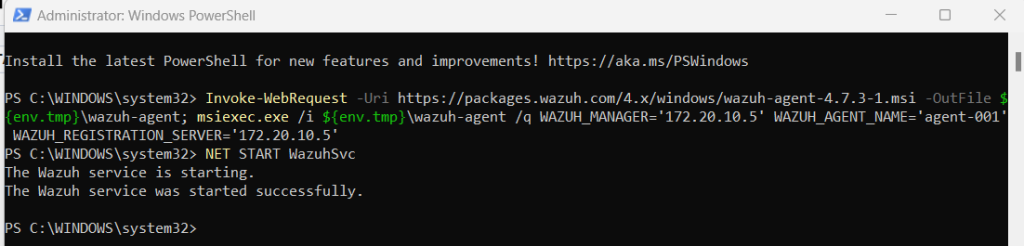
As you can see, the server is running so I entered the platform to begin setting up my first agent. The next steps included basic installation such as naming, address matching, and OS of choice. The following PowerShell script and command start the Wazuh service.
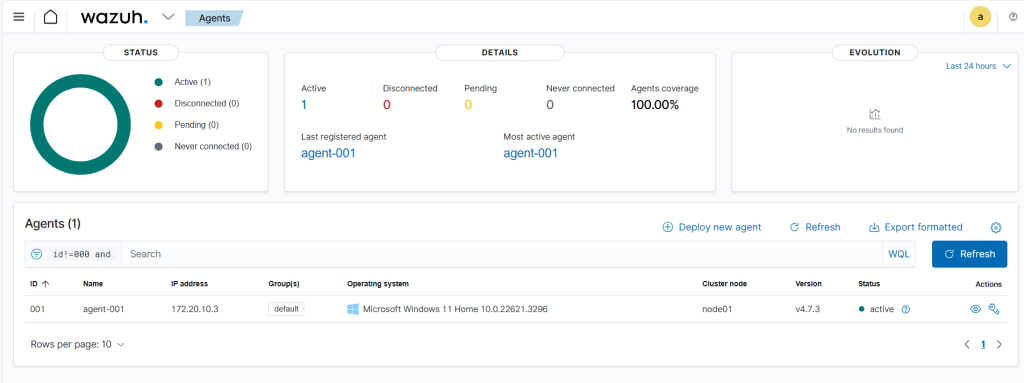
As seen below, my new Windows agent is running.
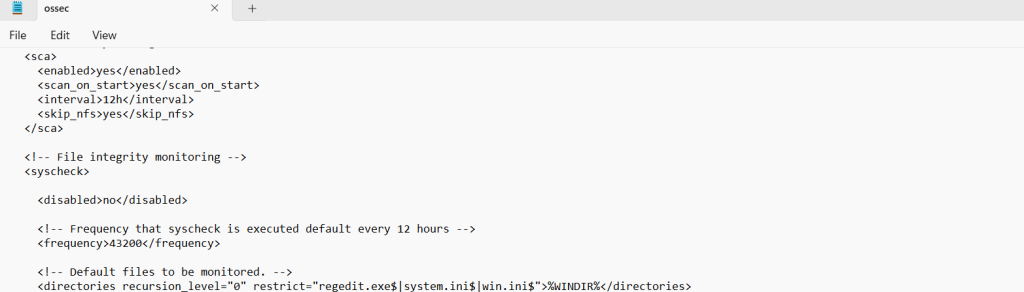
Now to the final step of enabling file Integrity, I came to find out it’s automatically enabled. The following is seen in the ossec configuration file where we see ‘no’ under the File Integrity monitoring which means it is enabled.
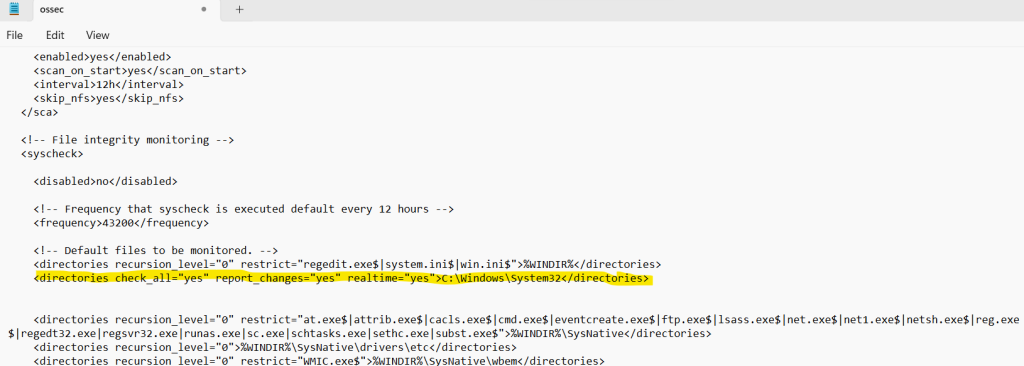
I chose to monitor any actions in the System32 folder considering its importance. The Systems32 folder holds important system files, dynamic link libraries, and executables that the Windows operating system needs to work properly.
An example would be when malware gets into a system, it tries to set up persistence so it can stay active and not be found. The malware changes or removes files in System32. Malware creators make their programs look like a part of the system so they go unseen.
I added the temp folder in the <directories tag>, highlighted below.
Now, if any files or changes are made in real-time, an alert will generate in the Security Alerts dashboard on the Wazuh platform. I will look into generating other rules based on scenarios, but this was an interesting and useful lab to simulate a defensive role.
Thanks for following along!